From SSTI to SSTI to RCE - Bypassing Thymeleaf sandbox <= 3.1.3.RELEASE
Abstract The Thymeleaf release version 3.0.12 came with improvements in its sandboxed evaluation process, by restricting objects creations and static functio...
This walkthrough presents another vulnerability discovered on the Mobatime web application (see CVE-2023-3032, same version 06.7.2022 affected). This vulnerability allows an authenticated user to impersonate another one, possibly having more privileges.
This application is essentially a single page, and the pieces of information are retrieved through AJAX calls. To get adequate pieces of information, the requests carry the user identifier, in order to fetch data related to them. The issue is that this identifier is controlled by the user, and the request body is not protected. It is therefore possible to change this identifier, and impersonate someone else.
A typical AJAX call is as follows:
POST /Webengine/api/ajax_api.aspx HTTP/1.1 Accept: */*
Accept-Encoding: gzip, deflate, br
... snipped ...
Sec-GPC: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.0.0
Safari/537.36 X-Requested-With: XMLHttpRequest
@64eyJhcnJheV9pbnQiOltdLCJmdW5jdGlvbiI6NTA3LCJpcGFyYW0xIjoxNTQsImlwYX
JhbTEwIjowLCJpcGFyYW0xMSI6MCwiaXBhcmFtMTIiOjAsImlwYXJhbTEzIjowLCJpcGF
yYW0xNCI6MCwiaXBhcmFtMTUiOjAsImlwYXJhbTIiOjg0MTUsImlwYXJhbTMiOjAsImlw
YXJhbTQiOjAsImlwYXJhbTUiOjAsImlwYXJhbTYiOjAsImlwYXJhbTciOjAsImlwYXJhb
TgiOjAsImlwYXJhbTkiOjAsImxwYXJhbTEiOjAsInBhcmFtMSI6IiIsInBhcmFtMiI6Ii
IsInBhcmFtMyI6IiIsInBhcmFtNCI6IiIsInBhcmFtNSI6IiIsInRva2VuIjowfQ==
One can recognise here a base64-encoded JSON (prefix eyJ), which gives us, once decoded:
{
"array_int":[],
"function":507,
"iparam1":154,
"iparam10":0,
"iparam11":0,
"iparam12":0,
"iparam13":0,
"iparam14":0,
"iparam15":0,
"iparam2":8415,
"iparam3":0,
"iparam4":0,
"iparam5":0,
"iparam6":0,
"iparam7":0,
"iparam8":0,
"iparam9":0,
"lparam1":0,
"param1":"",
"param2":"","
param3":"",
"param4":"",
"param5":"",
"token":0
}
Now, let’s assume that our ID is 154, and that we want to impersonate 155. Keen eye may see that the payload is not signed, hence forgeable. Since the application is a single page, it was likely that this value 154 was carried by a JS variable, and that we could change it at a single place. All subsequent AJAX calls would probably embed the modified ID, and make us act as 155.
Analysing the traffic reveals that the AJAX requests originate from a call to the routine Get in the file MobaBridge3.js. One can suppose here that this routine probably deals with the JSON payload so as to authenticated the request:
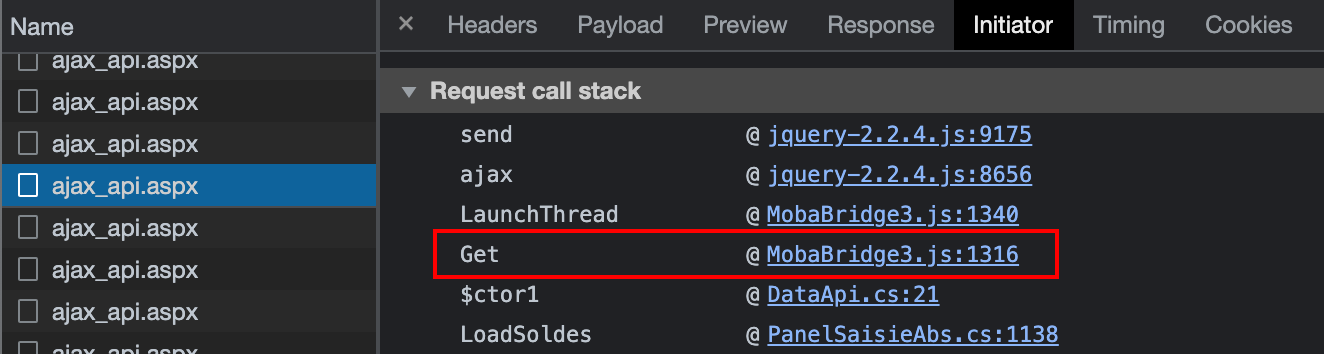
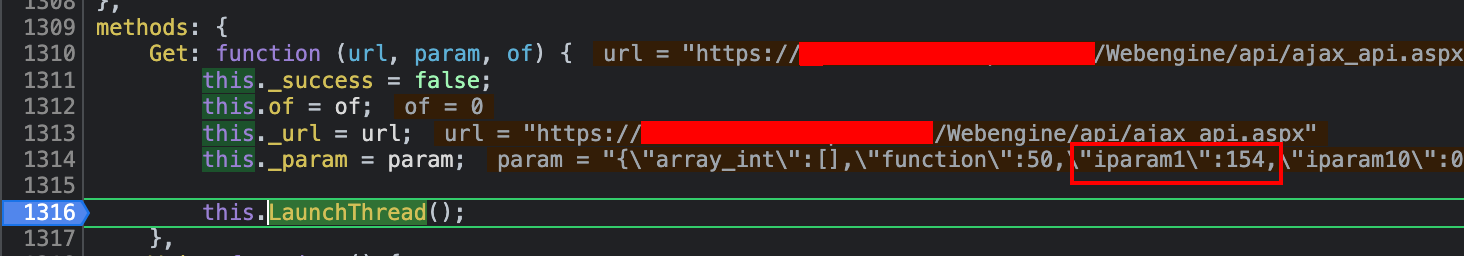
A breakpoint was therefore put at line 1’316, before the function end. Refreshing the page reveals that the attribute this._param holds the value 154. It comes from the second argument (param). Since the value 154 was already known there, one can step over LaunchThread to get back to the calling routine ($ctor1).
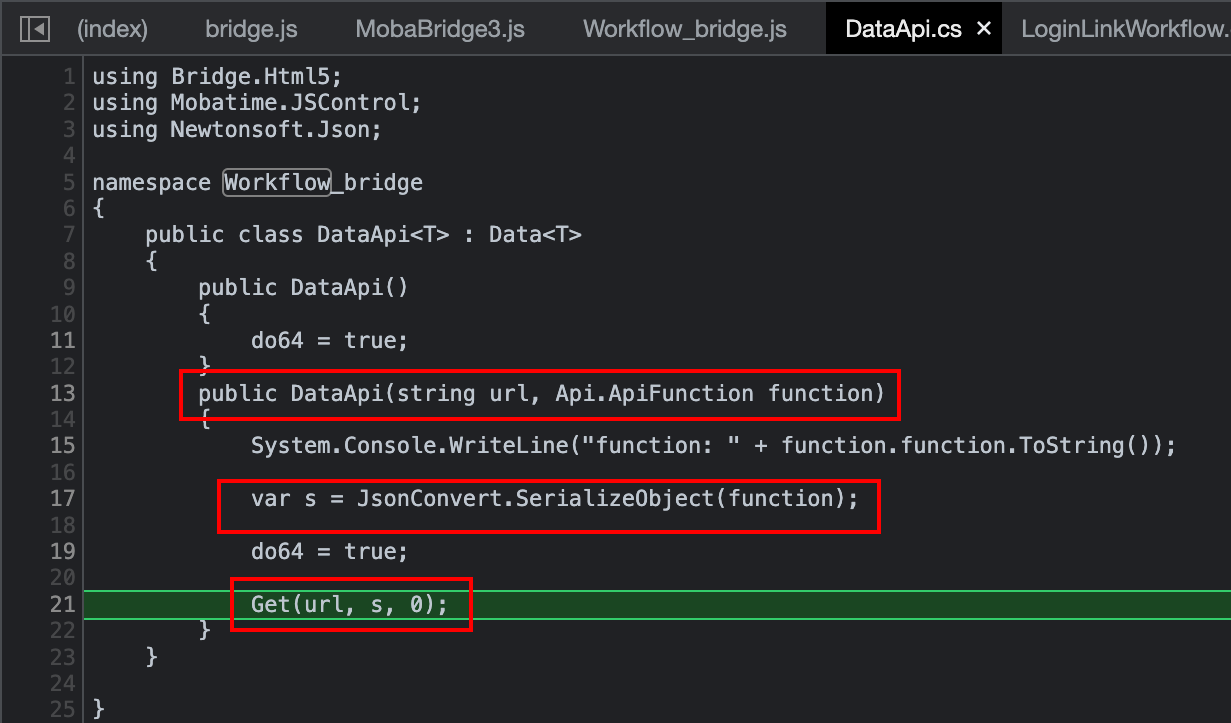
In this routine, a call to Get is indeed performed, and the second argument containing the identifier is referred to as s. The variable s is obtained thanks to a call to JsonConvert.SerializeObject, hence was likely to be built based on the variable function (line 17). The latter is passed as argument (line 13), and to analyse it, one should once again climb up the calling stack.
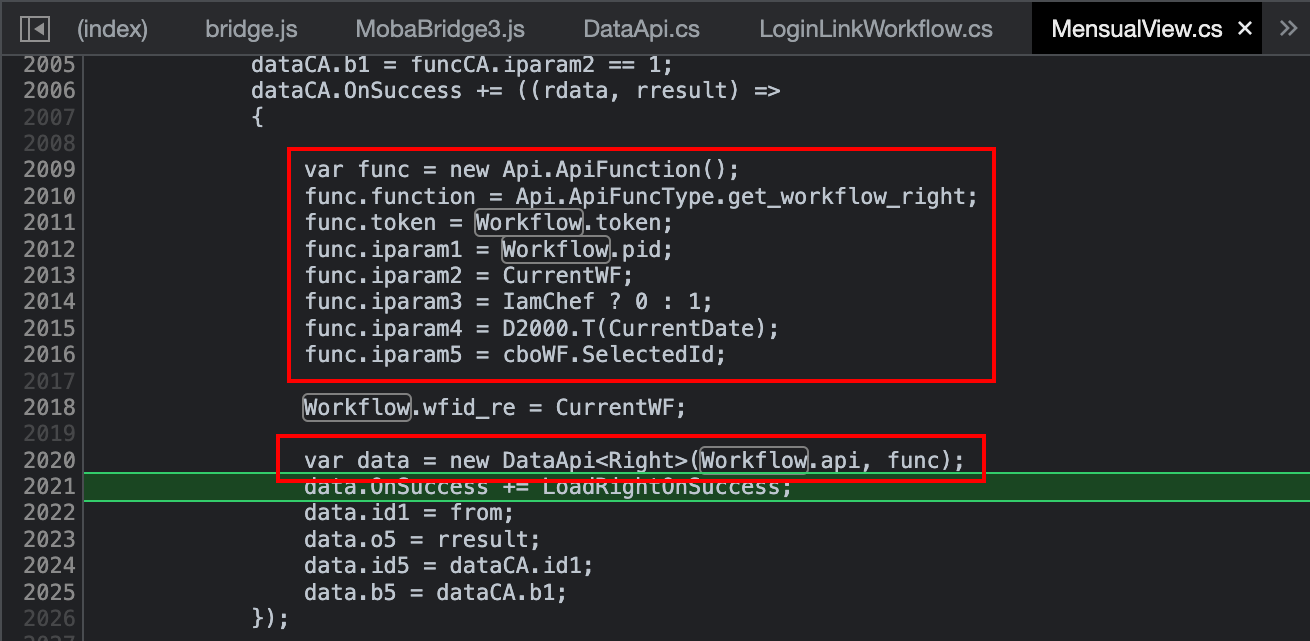
The caller lies in the class MensualView.cs, where the func variable is initialised (passed as function in the callee). It is worth noting that one of the attributes of func is named iparam1, just like the attribute carrying the identifier in the JSON stream. Its value is held by the attribute Workflow.pid. By looking where such variable is set thanks to a regular expression, only two results are returned. One of them lies on the class LoginLinkWorkflow.cs
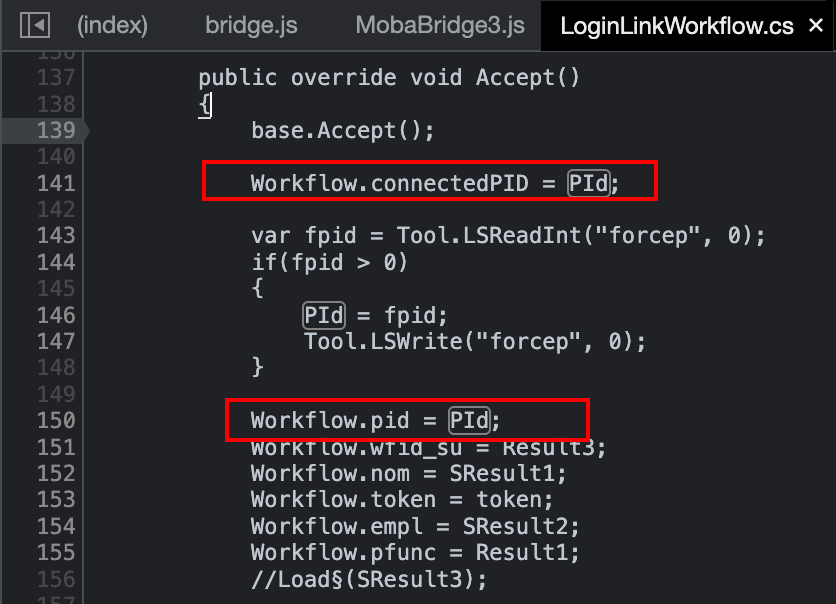
By putting a breakpoint at line 139 and refreshing the page, the breakpoint is hit. The value of the variable PId could be turned into 155, and letting the execution flow continue normally, and the page would be rendered as if we were 155.
Since only the advertised identifier seems to be used to verify the authorisations, a malicious user could trick the application into thinking that they are someone else by changing their ID on the client side. Since the server trusts this ID, they would serve inappropriate content. The server should use server-side variables to store the ID of a user, based on a session identifier. An alternative could make use of signed JWTs to make them inalterable.
Abstract The Thymeleaf release version 3.0.12 came with improvements in its sandboxed evaluation process, by restricting objects creations and static functio...
Abacus ERP is versions older than 2024.210.16036, 2023.205.15833, and 2022.105.15542 are affected by an authenticated arbitrary file read vulnerability. T...
It is a rainy Monday morning, and John is working from home, in his cozy apartment. He activated his VPN to access his business files, and everything is goin...
Intro When it comes to input sanitisation, who is responsible, the function or the caller ? Or both ? And if no one does, hoping that the other one will do t...
Intro After being tasked with auditing GLPI 10.0.12, for which I uncovered two unknown vulnerabilities (CVE-2024-27930 and CVE-2024-27937), I became really i...
Intro A few weeks ago, I discovered during an intrusion test two vulnerabilities affecting GLPI 10.0.12, that was the latest public version at this time. The...
I was recently tasked with auditing the application GLPI, a few days after its latest release (10.0.12 at the time of writing). The latter stands for Gestion...
I won’t insult you by explaining once again what JSON Web Tokens (JWTs) are, and how to attack them. A plethora of awesome articles exists on the Web, descri...
A few days ago, I published a blog post about PHP webshells, ending with a discussion about filters evasion by getting rid of the pattern $_. The latter is c...
A few thoughts about PHP webshells …
I remember this carpet, at the entrance of the Computer Science faculty, with this message There’s no place like 127.0.0.1/8. A joke that would create two ca...
TL;DR A few experiments about mixed managed/unmanaged assemblies. To begin with, we start by presenting a C# programme that hides a part of its payload in an...
It was a sunny and warm summer afternoon, and while normal people would rush to the beach, I decided to devote myself to one of my favourite activities: suff...
The reader should first take a look at the articles related to CVE-2023-3032 and CVE-2023-3033 that I published a few days ago to get more context.
This walkthrough presents another vulnerability discovered on the Mobatime web application (see CVE-2023-3032, same version 06.7.2022 affected). This vulnera...
Mobatime offers various time-related products, such as check-in solutions. In versions up to 06.7.2022, an arbitrary file upload allowed an authenticated use...
King-Avis is a Prestashop module developed by Webbax. In versions older than 17.3.15, the latter suffers from an authenticated path traversal, leading to loc...
Let’s render unto Caesar the things that are Caesar’s, the exploit FuckFastCGI is not mine and is a brilliant one, bypassing open_basedir and disable_functio...
I have to admit, PHP is not my favourite, but such powerful language sometimes really amazes me. Two days ago, I found a bypass of the directive open_basedir...
PHP is a really powerful language, and as a wise man once said, with great power comes great responsibilities. There is nothing more frustrating than obtaini...
A few weeks ago, a good friend of mine asked me if it was possible to create such a program, as it could modify itself. After some thoughts, I answered that ...
In the previous article, I described how I wrote a simple polymorphic program. “Polymorphic” means that the program (the binary) changes its appearance every...
The malware presented in this blog post appeared on Google Play in 2016. I heard about it thanks to this article published on checkpoint.com. The malicious a...
Ransomwares are really interesting malwares because of their very specific purpose. Indeed, a ransomware will not necessarily try to be stealth or persistent...
A few days ago, I found this article about a malware targeting Sberbank, a big Russian bank. The app disguises itself as a web application, stealing in backg...
RuMMS is a malware targetting Russian users, distributed via websites as a file named mms.apk [1]. This article is inspired by this analysis made by FireEye ...
Could a 5-classes Android app be so harmful ? dsencrypt says “yes”…
~$ cat How_an_Android_app_could_escalate_its_privileges_Part4.txt
~$ cat How_an_Android_app_could_escalate_its_privileges_Part3.txt
~$ cat How_an_Android_app_could_escalate_its_privileges_Part2.txt
~$ cat How_an_Android_app_could_escalate_its_privileges.txt
Even if the thesis introduces the extensions internals, and analyses the difference between mobile and desktop browsers in terms of likelihood, efficiency an...